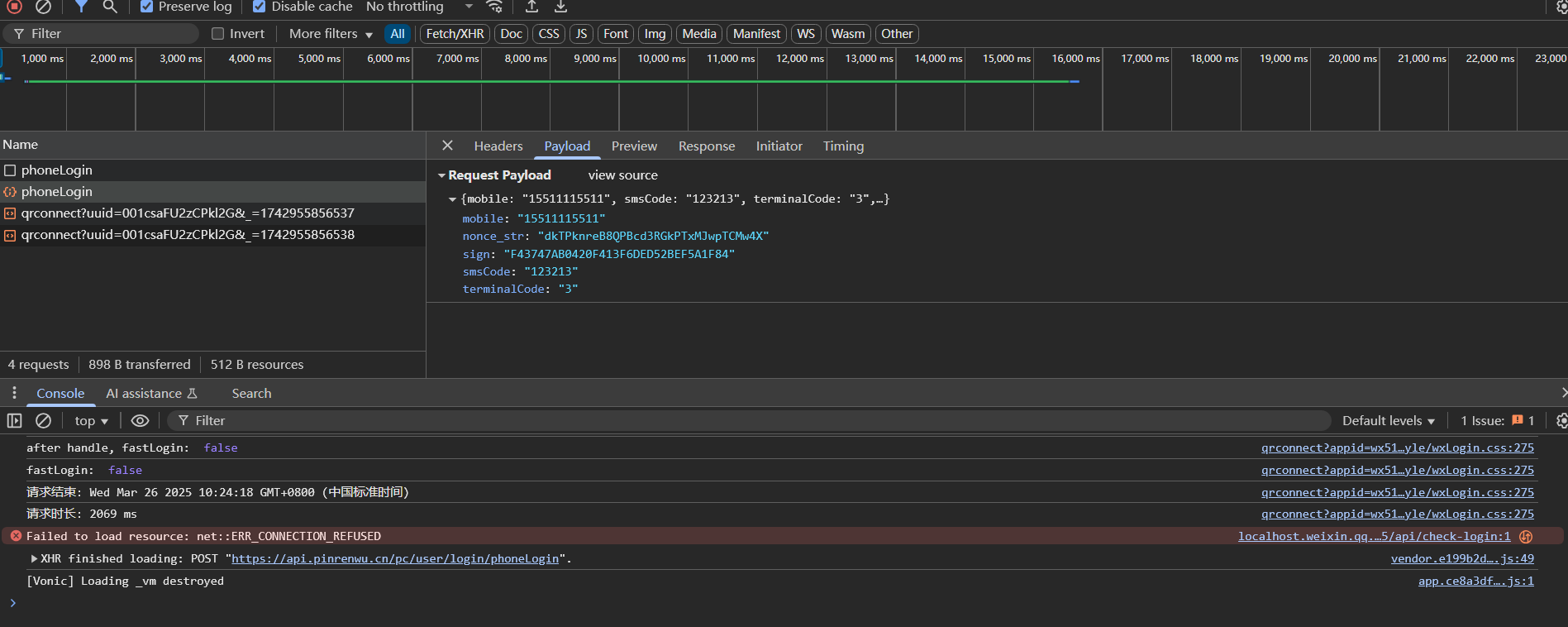
登录请求
有nonce_str和sign字段需要分析
在js文件中,一般有app.xxx.js或者vendor.xxx.js的文件名,都是webpack打包之后的js,webpack是什么?平时在开发的时候,不可能把代码都写在一个文件中,这样不利于维护,开发的时候肯定是分文件去写的,在发布的时候,webpack可以把不同文件的代码打包,打包后的文件会少很多
webpack分为两个部分,一个是模块,可以理解为模块在原始的源代码里,就是一个单独的文件,一个文件对应一个模块
另一个是模块加载器,也就是下面的n("Ds5P") ,n就是加载器,对于webpack代码的扣法,需要把加载器和对应的模块都给扣下来
1 | "7Jvp": function(t, e, n) { |
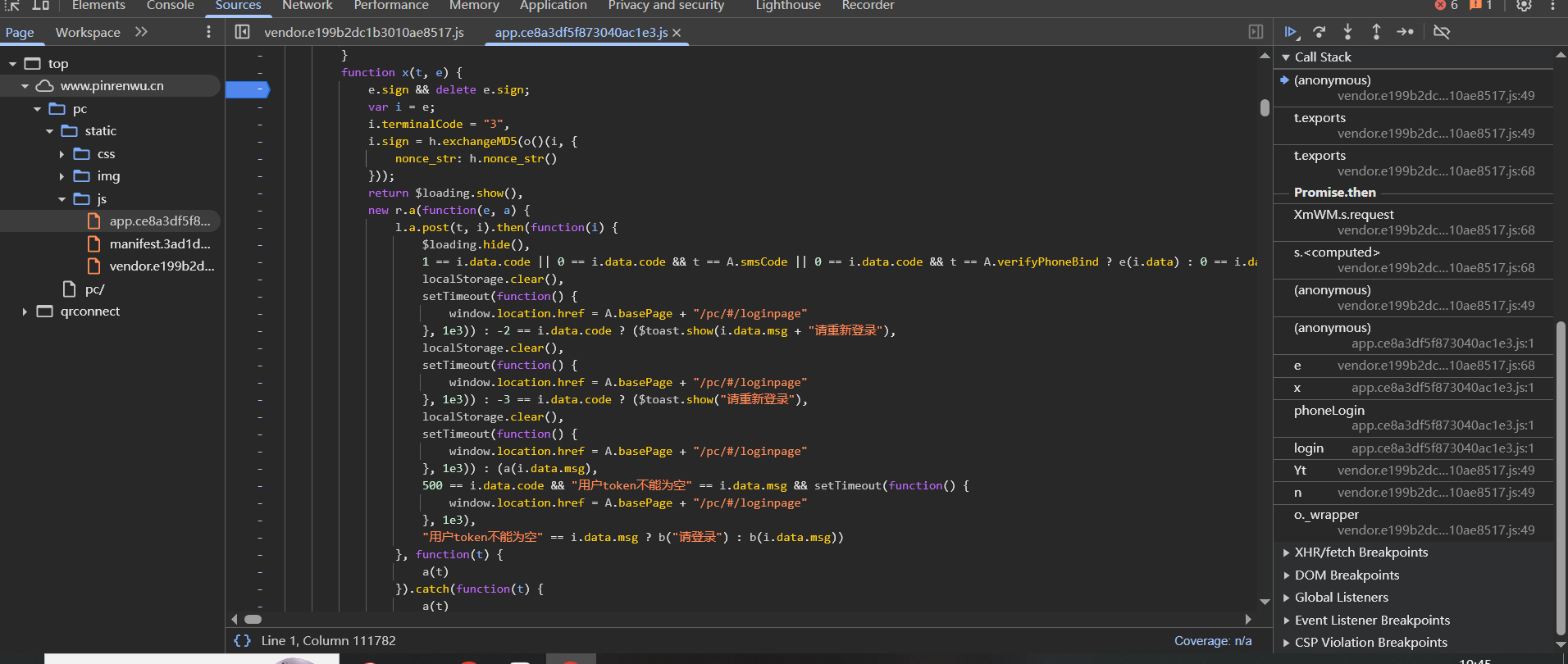
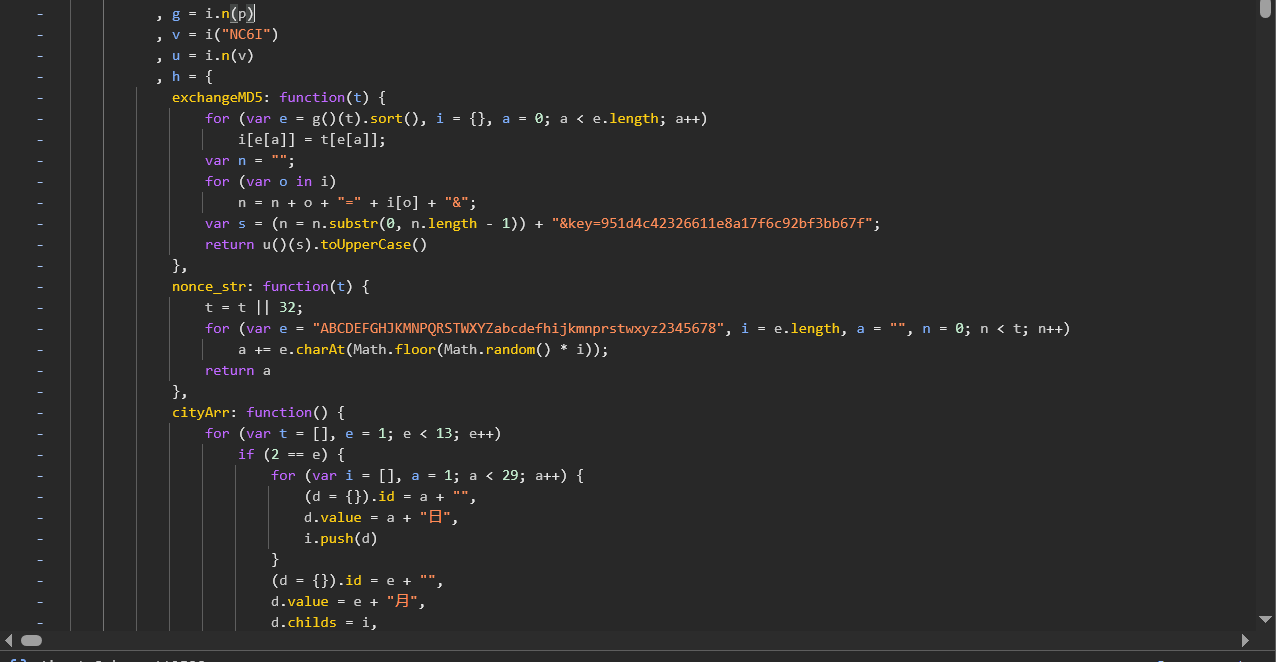
稍微跟一下,找到关键函数,可以看出来这里就是对sign参数赋值的
1 | i.sign = h.exchangeMD5(o()(i, { |
随后可以定位到生成nonce_str的函数
1 | , p = i("fZjL") |
这里u函数来自于v,v是通过模块加载器i加载的,在p = i("fZjL")处下断点,模块加载器是在网页加载的时候初始化的,刷新网页才能断下来,然后步入函数
扣的时候先把所有代码扣下来
1 | !function(r) { |
function t(n) 是加载模块,n是模块名,整个代码是一个匿名自执行函数,现在要做的是让这个匿名自执行函数能够根据模块名加载需要的模块,这里只定义了t函数,而不一定会调用它,所以需要把t函数给赋值给全局变量,在匿名函数外部去调用t函数
1 | let moduleImport; |
在t函数中,是通过 return r[n].call(o.exports, o, o.exports, t) 来调用的模块函数,r是匿名函数的参数,n可以理解为r参数的属性名,r[n]就是取属性的值进行调用,所以这里传入的参数r可以不是数组,改成对象就行,而且属性名就是模块名,属性值就是函数体,而且前面加密的函数模块名是NHnr,这个模块定义了很多函数,在扣的时候可以先扣核心加密代码
1 | NHnr: function(t, e, i) { |
修改一下代码,使代码符合语法,现在抠出来的加密代码如下
1 | let moduleImport; |
至此,模块导入已经全部实现了,现在还需要调用加密函数,加密函数在h函数处,还需要把这个函数赋值给全局变量,在外部调用
1 | let moduleImport,encParamObj; |
当然跑起来的时候,会报错少很多模块,需要手动一个个导入,导入的地方就在匿名函数的参数里去加属性名和值
自动化抠需要用到AST混淆还原,这个后面再说
抠webpack的流程就是,加载模块,调用加载模块函数去加载模块,然后执行加密代码