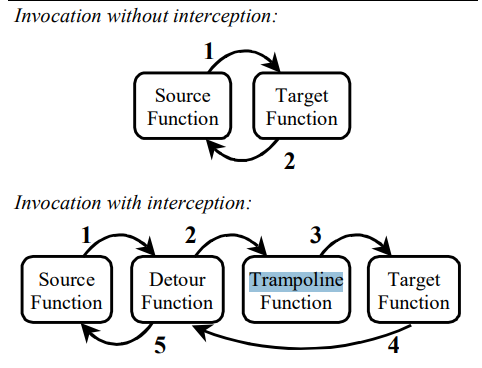
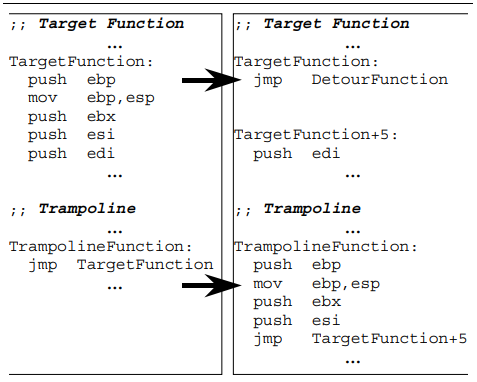
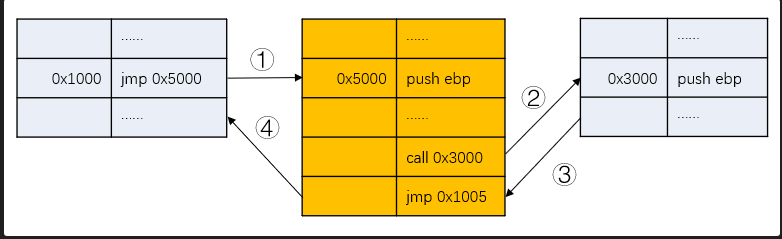
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
76
77
78
79
80
81
| #include <stdio.h>
#include <windows.h>
#include <dbghelp.h>
#pragma comment(lib, "user32.lib")
#pragma comment (lib, "dbghelp.lib")
#define ORIG_BYTES_SIZE 14
BOOL Hookem(FARPROC hookingFunc);
typedef int (WINAPI * OrigMessageBox_t)(HWND hWnd, LPCTSTR lpText, LPCTSTR lpCaption, UINT uType);
OrigMessageBox_t pOrigMessageBox = NULL;
char OriginalBytes[ORIG_BYTES_SIZE] = { 0 };
int HookedMessageBox(HWND hWnd, LPCTSTR lpText, LPCTSTR lpCaption, UINT uType) {
SIZE_T bytesOut = 0;
printf("HookedMessageBox() called. No popup on screen!\n");
WriteProcessMemory(GetCurrentProcess(), (LPVOID)pOrigMessageBox, OriginalBytes, ORIG_BYTES_SIZE, &bytesOut);
pOrigMessageBox(hWnd, lpText, lpCaption, uType);
Hookem((FARPROC) HookedMessageBox);
return IDOK;
}
BOOL Hookem(FARPROC hookingFunc) {
SIZE_T bytesIn = 0;
SIZE_T bytesOut = 0;
pOrigMessageBox = (OrigMessageBox_t) GetProcAddress(GetModuleHandle("user32.dll"), "MessageBoxA");
ReadProcessMemory(GetCurrentProcess(), pOrigMessageBox, OriginalBytes, ORIG_BYTES_SIZE, &bytesIn);
char patch[14] = { 0 };
memcpy(patch, "\xFF\x25", 2);
memcpy(patch + 6, &hookingFunc, 8);
WriteProcessMemory(GetCurrentProcess(), (LPVOID) pOrigMessageBox, patch, sizeof(patch), &bytesOut);
printf("IAT MessageBoxA() hooked!\n");
printf("HookedMessageBox @ %p ; OriginalBytes @ %p\n", HookedMessageBox, OriginalBytes);
return FALSE;
}
BOOL WINAPI DllMain(HINSTANCE hinst, DWORD dwReason, LPVOID reserved) {
switch (dwReason) {
case DLL_PROCESS_ATTACH:
Hookem((FARPROC) HookedMessageBox);
break;
case DLL_THREAD_ATTACH:
break;
case DLL_THREAD_DETACH:
break;
case DLL_PROCESS_DETACH:
break;
}
return TRUE;
}
|